Chert Security penetration testing provides insight into a malicious attacker’s mind.
Infrastructure Penetration testing is a proactive approach to discovering exploitable vulnerabilities in your computer systems and network as well as the devices within the network. Leveraging on proven methodologies, our approach goes beyond the use of automated tools and processes to include in-depth knowledge of how compromises can occur in government and commercial organizations.
Chert Security’s approaches attempt to search and identify flaws such as out of date software, missing patches, improper security configurations, weak communication algorithms, command injection, etc. Each of our penetration tests is customized for each client and thoroughly executed from the perspective of an adversary outside your organization as well as from the perspective of an insider threat. Our aim is to reveal any hidden threats and vulnerabilities so you can be a step ahead of the attacks, and also gives you the opportunity to address them.
Penetration testing is where security theory meets hacker reality.
Our penetration testing services are customized from ‘Black, White or Grey Box’ perspectives, depending on project needs.
Services Offered Include:
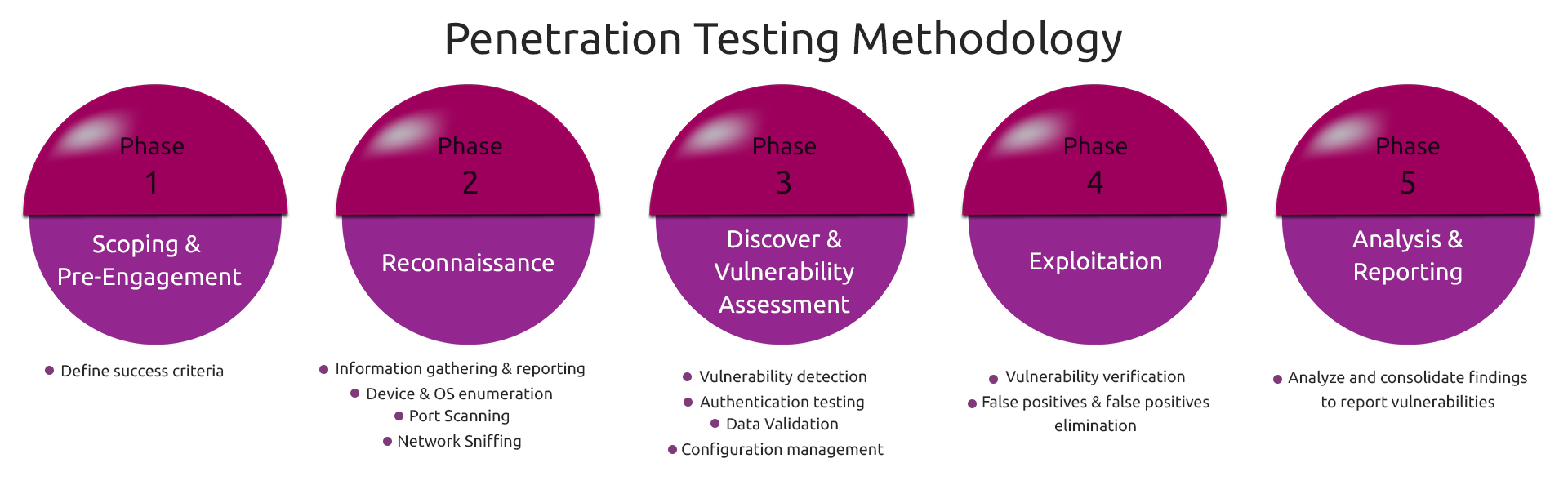
Our Penetration Testing Process
Chert Security’s penetration testing methodologies are comprehensive and drawn from industry standards such as OSSITM and involves the following key phases: